Trezor @Login Guide | Secure Access® to Your Crypto Wallet
Trezor Login is the secure gateway that allows you to access, manage, and protect your cryptocurrency through the Trezor hardware wallet and its companion Trezor Suite interface. It combines offline key storage with an intuitive dashboard so users can manage digital assets with confidence and ease.
What Is Trezor Login?
Trezor Login refers to the process of connecting your Trezor hardware wallet to Trezor Suite (desktop or web) to view balances, send and receive coins, and manage security settings. Instead of traditional usernames and passwords, access is authorized through your device PIN and optional passphrase, keeping private keys isolated from the internet.
When you log in, Trezor Suite establishes an encrypted connection with the hardware wallet, verifying actions directly on the device screen. This approach significantly reduces common attack vectors such as phishing, keylogging, and malware because sensitive data never leaves the hardware device.
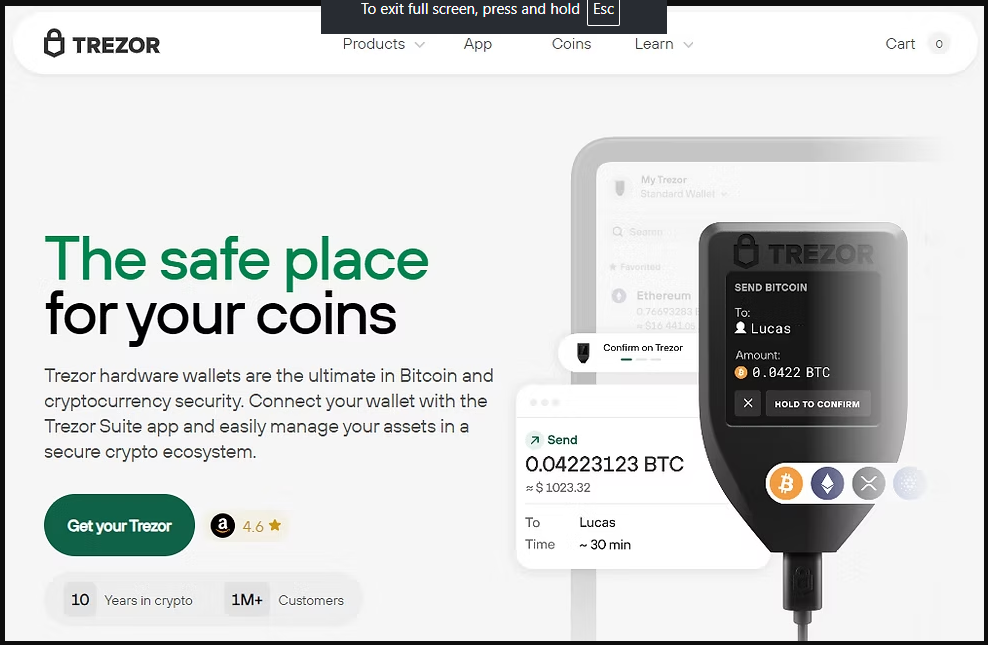
How Trezor Login Works
The login experience is designed to be simple enough for beginners, yet robust enough for experienced crypto users. Typically, you connect the device, open Trezor Suite, and authorize access by entering your PIN and confirming actions on the device itself. Once unlocked, the dashboard provides real-time portfolio tracking, transaction history, and tools for sending, receiving, buying, selling, and swapping supported assets.
Every critical operation, such as confirming a transaction or changing security settings, must be physically approved on the Trezor device. This requirement ensures that even if a computer is compromised, an attacker cannot move funds without the hardware wallet in hand.
Key Security Advantages
Trezor Login offers several important security advantages over software-only wallets and exchange accounts. First, private keys always remain offline inside the hardware wallet, significantly lowering the risk of online theft or exchange breaches. Second, the combination of PIN, optional passphrase, and physical confirmation creates multiple layers an attacker would need to bypass.
In addition, Trezor supports advanced privacy and security tools through Trezor Suite, including options like Tor integration, coin control, address verification on the device display, and protection against address‑poisoning attacks when sending funds. Many models also integrate FIDO2 or U2F capabilities, allowing the device to act as a secure second factor for logging in to other online services, further extending its role as a digital security hub.
User Experience and Convenience
Despite the strong security model, Trezor Login remains user‑friendly, with a clean interface suitable for both newcomers and advanced traders. The Trezor Suite layout makes it straightforward to check balances, review transaction history, and manage multiple cryptocurrencies from a single dashboard. Built‑in tools for exchange integrations and price insights help users monitor markets and manage their portfolios without constantly switching between platforms.
Because Trezor Suite is available as a desktop application and in-browser experience, users can choose the environment that best suits their workflow. After each session, disconnecting the device ensures that nothing sensitive remains exposed online, providing peace of mind between logins.
Benefits of Using Trezor Login
Trezor Login delivers a blend of high‑grade security and practical features that supports long‑term crypto management. The hardware‑based design and open‑source codebase give users transparency and control, reinforcing trust in how their assets are protected. Broad coin support and regular firmware updates mean that portfolios can grow and evolve without sacrificing safety or usability.
By requiring physical confirmation for logins and transactions, Trezor turns the simple act of signing in into a powerful defense against hacks and unauthorized access. For anyone serious about safeguarding digital wealth, using Trezor Login as the primary access point creates a solid foundation for secure, everyday crypto management.